Published September 26, 2025 | Author: everythingcryptoitclouds.com
The cryptocurrency trading landscape is experiencing a seismic shift, and at the epicenter of this transformation stands Dreamcash—a revolutionary mobile-first crypto wealth platform that’s redefining how we think about digital asset trading. With its tagline “Trading so good it feels like a dream,” Dreamcash isn’t just another trading app; it’s a comprehensive ecosystem that combines artificial intelligence, automated yield strategies, and zero-friction onboarding to democratize crypto wealth building for everyone.
In an industry where complexity has long been the barrier to entry, Dreamcash emerges as the solution that bridges the gap between sophisticated institutional-grade tools and the intuitive user experience that modern smartphone users demand. The platform launched its exclusive invite-only waitlist in August 2025, and the response has been nothing short of extraordinary—with over 40,000 signups and more than $500 million in pre-launch trading volume already recorded [1].
What makes Dreamcash particularly compelling is its strategic partnership with Hyperliquid, a proven infrastructure that processes over $10 billion in daily trading volume [2]. This partnership ensures that users have access to institutional-grade liquidity and execution from day one, while the platform’s AI-driven analytics provide insights that were previously available only to professional traders and hedge funds.
The timing of Dreamcash’s launch couldn’t be more perfect. As the cryptocurrency market continues to mature and institutional adoption accelerates, there’s a growing demand for platforms that can provide professional-grade tools without the complexity that has traditionally characterized crypto trading. Dreamcash addresses this need head-on with its mobile-first approach, recognizing that the future of finance is increasingly mobile and that users expect the same level of sophistication and ease of use from their trading platforms as they do from their favorite social media apps.
The Vision Behind Dreamcash: Democratizing Crypto Wealth Building
The fundamental vision driving Dreamcash is elegantly simple yet profoundly ambitious: to democratize crypto wealth building through intelligent tools, automated strategies, and zero-friction onboarding. This vision represents a departure from the traditional approach to cryptocurrency trading, which has often been characterized by steep learning curves, complex interfaces, and barriers that exclude all but the most technically sophisticated users.
Hubert Johnson, Head of Marketing at Dreamcash, articulates this vision with remarkable clarity: “We’re building the future of how people interact with crypto markets. Imagine having AI-driven insights, automated yield strategies, and professional-grade tools accessible through an interface as simple as your favorite social app” [3]. This statement encapsulates the core philosophy that drives every aspect of Dreamcash’s development—the belief that sophisticated financial tools should be accessible to everyone, not just institutional investors and crypto veterans.
The democratization of crypto wealth building represents more than just making trading more accessible; it’s about fundamentally changing the relationship between individuals and financial markets. Traditional wealth building has long been the domain of those with significant capital, extensive financial knowledge, or access to professional advisors. Dreamcash challenges this paradigm by providing tools that level the playing field, allowing anyone with a smartphone to access the same sophisticated strategies and insights that were previously available only to institutional investors.
This democratization is achieved through several key innovations that distinguish Dreamcash from traditional trading platforms. The platform’s AI-driven analytics provide users with market insights and opportunity identification that would typically require extensive research and analysis. The automated yield strategies eliminate the need for users to actively manage their positions, allowing them to benefit from sophisticated trading strategies without requiring deep technical knowledge. The zero-friction onboarding process removes the traditional barriers that have prevented many potential users from entering the crypto market.
The mobile-first design philosophy reflects a deep understanding of how modern users interact with technology. Rather than treating mobile as an afterthought or a simplified version of a desktop platform, Dreamcash has been designed from the ground up for mobile users. This approach recognizes that smartphones have become the primary computing device for most people and that the future of finance will be increasingly mobile-centric.
Revolutionary Features That Set Dreamcash Apart
Dreamcash’s revolutionary approach to crypto trading is built on several key features that collectively create an experience unlike anything currently available in the market. These features represent years of development and a deep understanding of both the technical requirements of sophisticated trading and the user experience expectations of modern mobile applications.
The AI-driven analytics system represents perhaps the most significant innovation in Dreamcash’s feature set. This system leverages advanced machine learning algorithms to analyze market data, identify trading opportunities, and provide users with actionable insights. The AI system is powered by a partnership with RysoAI, which brings institutional-grade artificial intelligence capabilities to retail users [4]. This partnership ensures that Dreamcash users have access to the same level of market analysis and opportunity identification that professional traders and hedge funds rely on.
The AI system operates continuously, monitoring market conditions across multiple cryptocurrencies and identifying patterns that might indicate profitable trading opportunities. Unlike traditional technical analysis tools that require users to interpret charts and indicators, Dreamcash’s AI system provides clear, actionable recommendations that users can act on with confidence. The system also learns from user behavior and market outcomes, continuously improving its recommendations and adapting to changing market conditions.
Automated yield strategies represent another groundbreaking feature that sets Dreamcash apart from traditional trading platforms. These strategies are designed to generate consistent returns regardless of market direction, using sophisticated techniques such as delta-neutral positioning and arbitrage opportunities. The automated nature of these strategies means that users can benefit from professional-grade trading techniques without needing to understand the underlying mechanics or actively manage their positions.
The delta-neutral strategies are particularly innovative, as they allow users to generate yield even in volatile or declining markets. These strategies work by taking offsetting positions that profit from market inefficiencies rather than directional price movements. This approach provides a level of stability and predictability that is rare in cryptocurrency trading, making it particularly attractive to users who want exposure to crypto markets without the extreme volatility typically associated with digital assets.
The zero-friction onboarding process eliminates many of the traditional barriers that have prevented mainstream adoption of cryptocurrency trading. Traditional crypto exchanges often require extensive know-your-customer (KYC) procedures, complex account setup processes, and significant technical knowledge just to begin trading. Dreamcash streamlines this process, allowing users to begin building their crypto portfolios immediately upon downloading the app.
This streamlined onboarding is achieved through innovative approaches to identity verification and risk management that maintain security while eliminating unnecessary friction. The platform uses advanced fraud detection and risk assessment algorithms to identify and prevent malicious activity while allowing legitimate users to access the platform quickly and easily. This approach represents a significant advancement in balancing security with user experience in the cryptocurrency space.
The Hyperliquid integration provides Dreamcash users with access to institutional-grade liquidity and execution capabilities. Hyperliquid is a proven infrastructure platform that processes over $10 billion in daily trading volume, providing deep liquidity across multiple cryptocurrency pairs [5]. This integration ensures that Dreamcash users can execute trades quickly and at competitive prices, even for large positions that might experience slippage on smaller exchanges.
The integration with Hyperliquid also provides access to advanced order types and trading features that are typically available only on professional trading platforms. These features include advanced stop-loss orders, trailing stops, and sophisticated position management tools that help users optimize their trading strategies and manage risk effectively.
The Points-Based Rewards System: Gamifying Crypto Engagement
One of the most innovative aspects of Dreamcash’s approach to user engagement is its comprehensive points-based rewards system, which gamifies the crypto trading experience while providing tangible benefits to early adopters. This system represents a sophisticated approach to user acquisition and retention that goes far beyond traditional referral programs or promotional offers.
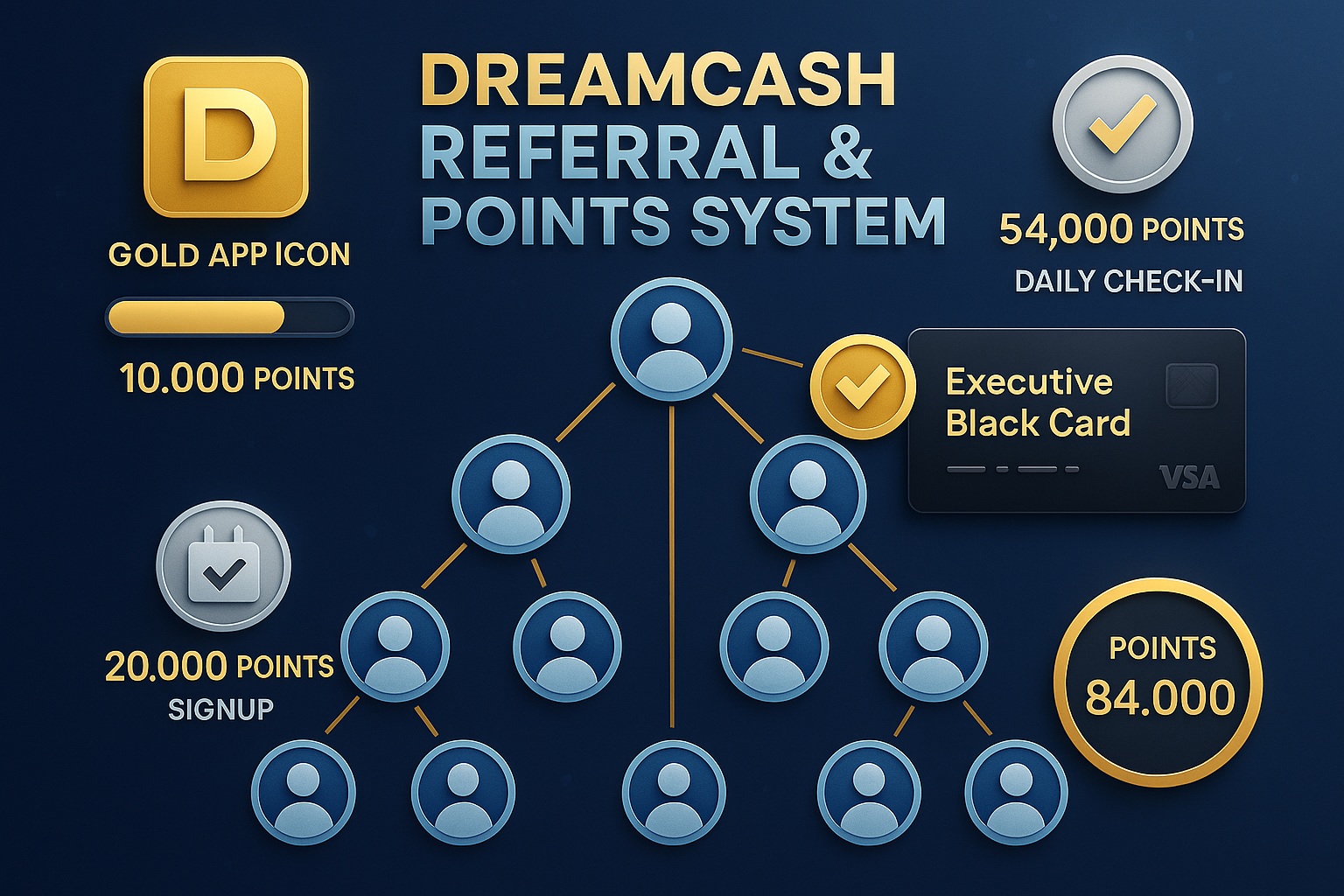
The points system operates on multiple levels, providing rewards for various types of engagement with the platform. Users earn one point per second simply for being on the waitlist, creating a passive income stream that rewards early adoption and continued engagement [6]. This passive earning mechanism ensures that users are continuously accumulating value even when they’re not actively using the platform, creating a strong incentive for long-term engagement.
Daily check-ins provide an additional 20,000 points, encouraging users to regularly interact with the app and stay engaged with the platform. This daily engagement mechanism helps build habits and ensures that users remain connected to the Dreamcash ecosystem even during the pre-launch phase. The substantial point reward for daily check-ins reflects the platform’s understanding of the value of consistent user engagement and the importance of building strong user habits early in the relationship.
The referral system provides the most substantial point rewards, with users earning 54,000 points for each successful referral [7]. This generous referral reward reflects the platform’s focus on organic growth and word-of-mouth marketing, recognizing that satisfied users are the best advocates for the platform. The referral system also creates a network effect, where each new user potentially brings additional users to the platform, accelerating growth and building a strong community of engaged users.
🎯 EXCLUSIVE OFFER: Use referral code TY74CU to get 10,000 FREE points when you sign up! Join Dreamcash with 10,000 bonus points
The exclusive rewards available through the points system add an element of prestige and exclusivity that appeals to early adopters. The Gold App Icon, available to users who achieve five or more referrals, provides a visible status symbol that distinguishes early supporters of the platform [8]. This exclusive reward will never be available again after the platform launches, creating a sense of urgency and exclusivity that motivates users to actively participate in the referral program.
The Executive Black Card, available to users who achieve ten or more referrals, represents the pinnacle of the pre-launch rewards system. This exclusive status symbol provides not only prestige but also potential access to additional platform benefits and features. Like the Gold App Icon, the Executive Black Card will never be available again after launch, making it a truly exclusive reward for the most engaged early adopters.
The points system is designed with future utility in mind, with strong indications that points will convert to platform benefits or potentially tokens after the official launch. While no official token airdrop has been confirmed, the structure and emphasis of the points system strongly suggest that early participants will receive lasting recognition and benefits for their early support of the platform [9].
Technical Infrastructure: The Hyperliquid Advantage
The technical foundation of Dreamcash is built on a strategic partnership with Hyperliquid, one of the most robust and proven infrastructure platforms in the cryptocurrency space. This partnership provides Dreamcash with access to institutional-grade capabilities that would be extremely difficult and expensive to develop independently, while allowing the platform to focus on user experience and innovation rather than infrastructure development.
Hyperliquid processes over $10 billion in daily trading volume, making it one of the largest and most liquid cryptocurrency trading infrastructures in the world [10]. This massive scale provides several critical advantages for Dreamcash users, including deep liquidity across multiple trading pairs, competitive pricing, and the ability to execute large trades without significant market impact. The scale of Hyperliquid’s operations also provides stability and reliability that is essential for a platform targeting mainstream adoption.
The liquidity provided by Hyperliquid is particularly important for the types of automated strategies that Dreamcash offers. Delta-neutral strategies and arbitrage opportunities often require the ability to execute trades quickly and at specific prices, making deep liquidity essential for their success. The Hyperliquid partnership ensures that Dreamcash’s automated strategies can operate effectively even during periods of high market volatility or unusual trading conditions.
The technical architecture of the Hyperliquid platform also provides advanced risk management and security features that are essential for institutional-grade trading. These features include sophisticated position monitoring, automated risk controls, and advanced security measures that protect user funds and trading positions. The proven track record of Hyperliquid in handling large volumes and maintaining security provides confidence that Dreamcash users’ assets and trading activities are protected by best-in-class infrastructure.
The integration between Dreamcash and Hyperliquid is designed to be seamless from the user perspective, with all the complexity of the underlying infrastructure hidden behind Dreamcash’s intuitive mobile interface. Users benefit from the sophisticated capabilities of Hyperliquid without needing to understand or interact with the technical complexities of the underlying system. This approach allows Dreamcash to provide institutional-grade capabilities with consumer-grade simplicity.
The Hyperliquid partnership also provides Dreamcash with access to advanced trading features and order types that are typically available only on professional trading platforms. These features include sophisticated stop-loss orders, trailing stops, and advanced position management tools that help users optimize their trading strategies and manage risk effectively. The availability of these advanced features through Dreamcash’s simple mobile interface represents a significant advancement in making professional trading tools accessible to retail users.
Market Position and Competitive Landscape
Dreamcash enters a cryptocurrency trading market that is both highly competitive and rapidly evolving, with established players ranging from traditional exchanges like Coinbase and Binance to newer mobile-first platforms like Robinhood and newer entrants. However, Dreamcash’s unique combination of features and approach creates a distinct market position that differentiates it from existing competitors.
The mobile-first approach represents a significant competitive advantage in a market where most established platforms were originally designed for desktop use and later adapted for mobile. While many existing platforms offer mobile apps, these are often simplified versions of their desktop platforms or mobile adaptations that don’t fully leverage the unique capabilities and user experience expectations of mobile devices. Dreamcash’s ground-up mobile design allows it to provide a user experience that is optimized for how people actually use their smartphones.
The AI-driven analytics and automated strategies represent another significant competitive differentiator. While some platforms offer basic technical analysis tools or simple automated features, Dreamcash’s partnership with RysoAI provides access to institutional-grade artificial intelligence capabilities that are not available on other retail platforms [11]. This AI integration provides users with insights and opportunities that would typically require extensive research and analysis, creating a significant value proposition for users who want to benefit from sophisticated trading strategies without developing the expertise to implement them independently.
The zero-friction onboarding process addresses one of the most significant barriers to entry in the cryptocurrency market. Traditional exchanges often require extensive documentation, verification processes, and waiting periods before users can begin trading. Dreamcash’s streamlined approach allows users to begin building their crypto portfolios immediately, removing a major source of friction that prevents many potential users from entering the market.
The points-based rewards system and gamification elements also represent a unique approach to user engagement that is not commonly found in traditional cryptocurrency trading platforms. While some platforms offer referral bonuses or promotional rewards, Dreamcash’s comprehensive points system creates ongoing engagement and provides lasting value to early adopters. This approach helps build a strong community of engaged users who have a vested interest in the platform’s success.
The integration with Hyperliquid provides access to liquidity and execution capabilities that rival or exceed those available on major exchanges, while the mobile-first design and user experience innovations provide a level of accessibility and ease of use that is not available on traditional institutional platforms. This combination allows Dreamcash to compete effectively with both retail-focused platforms and institutional-grade trading systems.
The Future of Mobile Crypto Trading
Dreamcash represents more than just another trading platform; it embodies a vision of the future of cryptocurrency trading that is mobile-first, AI-powered, and accessible to everyone. The platform’s approach reflects several key trends that are reshaping the financial services industry and points toward a future where sophisticated financial tools are available to anyone with a smartphone.
The mobile-first approach reflects the reality that smartphones have become the primary computing device for most people around the world. This trend is particularly pronounced among younger demographics, who are increasingly comfortable conducting all aspects of their financial lives through mobile devices. Dreamcash’s recognition of this trend and its commitment to providing a truly mobile-native experience positions it well to capture this growing market segment.
The integration of artificial intelligence into trading and investment decisions represents another major trend that is reshaping the financial services industry. As AI technology continues to advance and become more accessible, platforms that can effectively leverage AI to provide value to users will have a significant competitive advantage. Dreamcash’s partnership with RysoAI and its focus on AI-driven analytics positions it at the forefront of this trend.
The democratization of sophisticated financial tools is another key trend that Dreamcash embodies. Traditional wealth management and sophisticated trading strategies have long been available only to high-net-worth individuals and institutional investors. Technology is increasingly making these tools accessible to a broader audience, and platforms that can effectively democratize access to sophisticated financial strategies will capture significant market share.
The gamification of financial services is an emerging trend that Dreamcash has embraced through its points-based rewards system. As younger generations become a larger portion of the investing population, platforms that can make financial services engaging and rewarding will have an advantage in attracting and retaining users. Dreamcash’s comprehensive gamification approach goes beyond simple rewards to create an engaging experience that encourages long-term participation.
The focus on user experience and simplicity represents a broader trend in financial services toward platforms that prioritize ease of use and accessibility. As financial services become increasingly digital, platforms that can provide sophisticated capabilities through simple, intuitive interfaces will have a significant advantage. Dreamcash’s commitment to making professional-grade tools accessible through a simple mobile interface positions it well to benefit from this trend.
Getting Started: Your Path to 10,000 Free Points
For readers interested in joining the Dreamcash revolution, the process is straightforward and rewarding. The platform’s invite-only waitlist provides early access to the platform and the opportunity to begin accumulating points immediately. The points system provides multiple ways to earn rewards, with the potential for these points to convert to lasting benefits or tokens after the platform’s official launch.
Step 1: Download and Register
The first step is to download the Dreamcash app from the App Store or Google Play and complete the registration process. During registration, be sure to enter the referral code TY74CU to receive an immediate bonus of 10,000 points Join here with bonus points. This bonus provides a significant head start in the points accumulation process and demonstrates the platform’s commitment to rewarding early adopters.
Step 2: Begin Earning Points
Once registered, users automatically begin earning one point per second simply for being on the waitlist. This passive earning mechanism ensures that points accumulate continuously, even when users are not actively engaging with the app. The passive earning rate may seem small, but it adds up significantly over time, particularly for early adopters who join during the pre-launch phase.
Step 3: Daily Engagement
Daily check-ins provide an additional 20,000 points, making regular engagement with the app highly rewarding. The daily check-in process is simple and quick, requiring just a few seconds of interaction with the app. However, the point reward is substantial, making daily engagement one of the most efficient ways to accumulate points quickly.
Step 4: Social Media Engagement
Following Dreamcash on social media platforms provides additional point bonuses and helps users stay informed about platform developments and updates. The social media engagement rewards recognize the value of building a strong community around the platform and encourage users to become advocates for Dreamcash within their social networks.
Step 5: Referral Activity
The referral program provides the most substantial point rewards, with 54,000 points awarded for each successful referral. Users receive a unique referral code that they can share with friends, family, and social networks. The generous referral rewards make sharing the platform with others highly beneficial, while also helping to build the Dreamcash community through organic growth.
Step 6: Exclusive Rewards
Users who achieve five or more referrals unlock the Gold App Icon, while those who achieve ten or more referrals receive the Executive Black Card. These exclusive rewards will never be available again after the platform launches, making them truly unique status symbols for early adopters. The exclusive nature of these rewards creates additional motivation for active participation in the referral program.
Investment Implications and Market Opportunity
The emergence of Dreamcash represents a significant development in the cryptocurrency trading space with important implications for investors, traders, and the broader digital asset ecosystem. The platform’s innovative approach to mobile trading, AI integration, and user experience represents a new paradigm that could influence the development of the entire cryptocurrency trading industry.
From an investment perspective, Dreamcash’s approach addresses several key pain points that have limited mainstream adoption of cryptocurrency trading. The complexity of traditional trading platforms, the lack of sophisticated tools for retail users, and the barriers to entry created by cumbersome onboarding processes have all contributed to limiting the growth of the cryptocurrency trading market. Dreamcash’s solutions to these problems position it to capture significant market share as cryptocurrency adoption continues to grow.
The total addressable market for cryptocurrency trading continues to expand rapidly, driven by increasing institutional adoption, growing retail interest, and the development of new financial products and services built on blockchain technology. Platforms that can effectively serve this growing market while providing superior user experience and innovative features are likely to capture disproportionate value as the market continues to mature.
The AI integration and automated strategies offered by Dreamcash also represent a significant advancement in making sophisticated trading techniques accessible to retail users. As artificial intelligence technology continues to advance and become more accessible, platforms that can effectively leverage AI to provide value to users will have a significant competitive advantage. The partnership with RysoAI positions Dreamcash at the forefront of this trend.
The mobile-first approach reflects broader trends in how people interact with financial services and technology. As smartphone adoption continues to grow globally and younger generations become a larger portion of the investing population, platforms that are designed specifically for mobile use will have significant advantages over those that treat mobile as an afterthought.
The points-based rewards system and potential for future token distribution also create interesting dynamics for early adopters. While no official token airdrop has been confirmed, the structure of the points system and the emphasis on early adoption suggest that participants in the pre-launch program may receive significant benefits when the platform officially launches. This creates an asymmetric risk-reward opportunity for early participants.
Conclusion: The Dawn of a New Era in Crypto Trading
Dreamcash represents more than just another cryptocurrency trading platform; it embodies a vision of the future where sophisticated financial tools are accessible to everyone, where artificial intelligence enhances human decision-making, and where mobile technology enables seamless interaction with global financial markets. The platform’s innovative approach to user experience, technical infrastructure, and community building positions it as a potential leader in the next generation of cryptocurrency trading platforms.
The combination of AI-driven analytics, automated yield strategies, zero-friction onboarding, and mobile-first design creates a unique value proposition that addresses many of the barriers that have limited mainstream adoption of cryptocurrency trading. The strategic partnership with Hyperliquid provides the technical foundation necessary to deliver institutional-grade capabilities through a consumer-friendly interface.
The points-based rewards system and focus on community building demonstrate a sophisticated understanding of user engagement and the importance of creating lasting relationships with users. The exclusive rewards available to early adopters create strong incentives for participation while building a community of engaged advocates for the platform.
For individuals interested in participating in the future of cryptocurrency trading, Dreamcash offers an opportunity to join a revolutionary platform during its early stages. The generous rewards for early adoption, combined with the potential for lasting benefits from the points system, create compelling reasons to participate in the pre-launch program.
The cryptocurrency trading industry is at an inflection point, with increasing institutional adoption, growing retail interest, and rapid technological advancement creating opportunities for platforms that can effectively serve this evolving market. Dreamcash’s innovative approach and strong technical foundation position it well to capitalize on these trends and potentially become a leader in the next generation of cryptocurrency trading platforms.
As we look toward the future of finance, platforms like Dreamcash that prioritize accessibility, innovation, and user experience will play an increasingly important role in democratizing access to sophisticated financial tools and opportunities. The revolution in cryptocurrency trading has begun, and Dreamcash is positioned at the forefront of this transformation.
Ready to join the revolution? Use referral code TY74CU to get 10,000 FREE points and be part of the future of crypto trading: https://dreamcash.xyz/share?code=TY74CU
References
[1] ETF.com – “Dreamcash Begins Rollout of Trading Platform with Hyperliquid Integration via Waitlist Access” (August 5, 2025) – https://www.etf.com/sections/news/dreamcash-begins-rollout-trading-platform-hyperliquid-integration-waitlist-access
[2] Yahoo Finance – “Dreamcash Begins Rollout of Trading Platform with Hyperliquid Integration” (August 5, 2025) – https://finance.yahoo.com/news/dreamcash-begins-rollout-trading-platform-221040657.html
[3] ETF.com – “Dreamcash Begins Rollout of Trading Platform with Hyperliquid Integration via Waitlist Access” (August 5, 2025)
[4] Bitrue Blog – “Dreamcash Airdrop: A Complete Guide for Early Participants” (September 17, 2025) – https://www.bitrue.com/blog/how-to-participate-dreamcash-airdrop
[5] ETF.com – “Dreamcash Begins Rollout of Trading Platform with Hyperliquid Integration via Waitlist Access” (August 5, 2025)
[6] Bitrue Blog – “Dreamcash Airdrop: A Complete Guide for Early Participants” (September 17, 2025)
[7] Bitrue Blog – “Dreamcash Airdrop: A Complete Guide for Early Participants” (September 17, 2025)
[8] Bitrue Blog – “Dreamcash Airdrop: A Complete Guide for Early Participants” (September 17, 2025)
[9] Airdrops.io – “Potential Dreamcash Airdrop » How to be eligible?” – https://airdrops.io/dreamcash/
[10] ETF.com – “Dreamcash Begins Rollout of Trading Platform with Hyperliquid Integration via Waitlist Access” (August 5, 2025)
[11] Bitrue Blog – “Dreamcash Airdrop: A Complete Guide for Early Participants” (September 17, 2025)