Published October 8, 2025 | Author: everythingcryptoitclouds.com
In one of the most remarkable corporate transformation stories in cryptocurrency history, CleanCore Solutions (NYSE: ZONE) has evolved from a traditional cleaning and disinfection company into a formidable Dogecoin treasury firm, amassing over 710 million DOGE tokens worth approximately $174 million in just over one month. This extraordinary pivot represents not just a strategic business decision, but a bold bet on the future of cryptocurrency as a legitimate treasury asset and the potential for meme coins to achieve institutional legitimacy.
The journey from cleaning supplies to cryptocurrency treasury management began on September 5, 2025, when CleanCore officially launched its “Official Dogecoin Treasury” strategy, raising $175 million through a private placement and setting an ambitious goal of accumulating 1 billion DOGE tokens within 30 days [1]. What followed was one of the most aggressive and successful cryptocurrency accumulation campaigns in corporate history, demonstrating both the company’s commitment to its new strategy and the market’s appetite for institutional Dogecoin adoption.
As of October 7, 2025, CleanCore has achieved 71% of its ambitious 1 billion DOGE milestone, holding over 710 million tokens with unrealized gains exceeding $20 million since the strategy’s launch [2]. This remarkable achievement places CleanCore among the largest institutional holders of Dogecoin and represents a validation of the company’s thesis that the popular meme coin has evolved beyond its origins to become a legitimate store of value and utility asset.
The transformation of CleanCore from a traditional cleaning company to a cryptocurrency treasury firm reflects broader trends in corporate finance, where companies are increasingly looking beyond traditional assets to hedge against inflation, currency devaluation, and economic uncertainty. However, CleanCore’s choice of Dogecoin over more established cryptocurrencies like Bitcoin or Ethereum represents a particularly bold and contrarian bet that has captured the attention of both cryptocurrency enthusiasts and traditional investors.
The strategic rationale behind CleanCore’s Dogecoin treasury strategy extends beyond simple speculation or trend-following. The company has positioned itself as a pioneer in institutional Dogecoin adoption, working closely with the Dogecoin Foundation through its House of Doge partnership to advance the ecosystem’s development and utility [3]. This collaborative approach suggests that CleanCore views its investment not just as a financial play, but as a strategic positioning for the future of digital payments and decentralized finance.
The Anatomy of a Corporate Transformation

The transformation of CleanCore Solutions from a traditional cleaning company to a cryptocurrency treasury firm represents one of the most dramatic corporate pivots in recent business history, rivaling the strategic shifts undertaken by companies like MicroStrategy in the Bitcoin space. Understanding the mechanics and timeline of this transformation provides crucial insights into how traditional businesses can successfully navigate the transition to cryptocurrency-focused strategies.
The foundation for CleanCore’s transformation was laid through a series of strategic moves that began well before the official launch of the Dogecoin treasury strategy. On September 2, 2025, just three days before the treasury launch, Alex Spiro, who serves as Elon Musk’s attorney, became Chairman of CleanCore’s Board of Directors [4]. This appointment was far from coincidental, as Spiro’s close relationship with Musk, one of Dogecoin’s most prominent advocates, provided both credibility and strategic guidance for the company’s cryptocurrency ambitions.
The timing of Spiro’s appointment and the subsequent treasury launch suggests careful planning and coordination that extends beyond simple investment strategy. Spiro’s involvement brings not only legal expertise in cryptocurrency matters but also connections to the broader ecosystem of Dogecoin supporters and developers. This network effect has proven crucial in establishing CleanCore’s credibility within the Dogecoin community and securing the partnerships necessary for successful treasury management.
The financial mechanics of CleanCore’s transformation were equally impressive, with the company successfully raising $175 million through a private placement that attracted over 80 institutional participants [5]. This fundraising achievement is particularly noteworthy given CleanCore’s relatively modest size and limited track record in cryptocurrency investments. The success of this capital raise reflects both the growing institutional interest in cryptocurrency exposure and the market’s confidence in CleanCore’s strategic vision and execution capabilities.
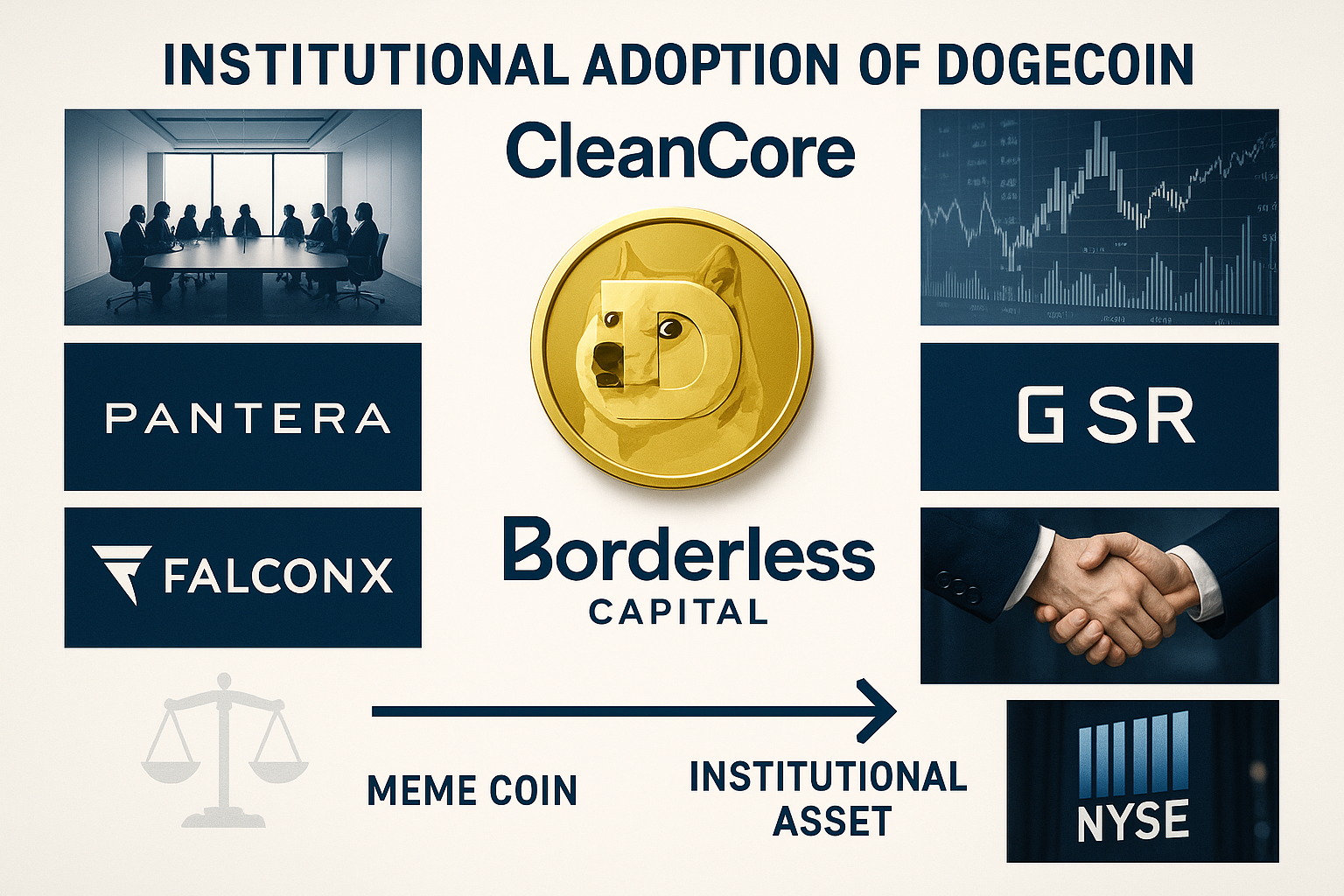
The investor base for CleanCore’s private placement reads like a who’s who of cryptocurrency and venture capital, including prominent names such as Pantera Capital, GSR, FalconX, and Borderless Capital [6]. The participation of these sophisticated institutional investors provides validation of CleanCore’s strategy and creates a network of strategic partners who can provide ongoing support and guidance as the company executes its treasury management plan.
The operational transformation required to support CleanCore’s new strategy has been equally comprehensive, with the company establishing new partnerships and infrastructure to manage its cryptocurrency holdings effectively. The designation of Bitstamp by Robinhood as the primary trading venue and custodian for CleanCore’s Dogecoin holdings represents a crucial element of this infrastructure, providing institutional-grade security and compliance capabilities [7].
The partnership with the Dogecoin Foundation through the House of Doge initiative represents another critical component of CleanCore’s transformation strategy. This collaboration goes beyond simple investment management to encompass ecosystem development, governance participation, and strategic positioning within the broader Dogecoin community. The House of Doge partnership provides CleanCore with access to technical expertise, development resources, and strategic guidance that enhance the value and utility of its Dogecoin holdings.
The leadership changes accompanying CleanCore’s transformation reflect the company’s commitment to building the expertise necessary for successful cryptocurrency treasury management. The appointment of Marco Margiotta as Chief Investment Officer has provided the company with dedicated leadership for its cryptocurrency strategy, while maintaining continuity in its traditional cleaning business operations [8]. This dual-track approach allows CleanCore to pursue its cryptocurrency ambitions while preserving the cash flows and operational capabilities of its core business.
The speed and scale of CleanCore’s Dogecoin accumulation have been remarkable by any standard, with the company acquiring 285.42 million DOGE tokens in its initial purchase on September 8, 2025, just three days after launching the strategy [9]. This aggressive approach continued throughout September, with the company crossing the 500 million DOGE threshold on September 11 and reaching 600 million tokens by September 16. The sustained pace of accumulation demonstrates both the company’s commitment to its strategy and its ability to execute large-scale cryptocurrency transactions efficiently.
Strategic Partnerships and Institutional Validation
The success of CleanCore’s Dogecoin treasury strategy has been significantly enhanced by a carefully constructed network of strategic partnerships that provide both operational capabilities and institutional credibility. These partnerships represent more than simple service provider relationships; they constitute a comprehensive ecosystem of support that enables CleanCore to execute its ambitious cryptocurrency strategy while maintaining the highest standards of security, compliance, and operational excellence.
The partnership with the Dogecoin Foundation through the House of Doge initiative represents the cornerstone of CleanCore’s strategic positioning within the Dogecoin ecosystem. This collaboration provides CleanCore with direct access to the technical development roadmap, governance processes, and strategic planning that shape Dogecoin’s future evolution [10]. The House of Doge partnership also positions CleanCore as a key stakeholder in ecosystem development initiatives, potentially creating opportunities for yield generation and value creation beyond simple token appreciation.
The relationship with Bitstamp by Robinhood as the designated trading venue and custodian represents another crucial element of CleanCore’s partnership strategy. Bitstamp’s institutional-grade infrastructure provides the security, compliance, and operational capabilities necessary to manage large-scale cryptocurrency holdings safely and efficiently [11]. The choice of Bitstamp also reflects CleanCore’s commitment to working with established, regulated entities that can provide the institutional credibility necessary for corporate treasury management.
The custodial arrangements with Bitstamp include sophisticated security measures such as multi-signature wallets, cold storage protocols, and comprehensive insurance coverage that protect CleanCore’s holdings against both technical failures and security breaches. These protections are essential for institutional investors who require the same level of security and risk management for cryptocurrency holdings as they would expect for traditional financial assets.
The institutional investor base that participated in CleanCore’s $175 million private placement represents a powerful validation of the company’s strategy and provides ongoing strategic support for its cryptocurrency initiatives. The participation of Pantera Capital, one of the most respected cryptocurrency investment firms, brings not only capital but also strategic guidance and network access that can enhance CleanCore’s positioning within the broader cryptocurrency ecosystem [12].
GSR’s participation as both an investor and potential market-making partner provides CleanCore with access to sophisticated trading and liquidity management capabilities that can optimize the execution of its accumulation strategy and ongoing treasury management activities [13]. GSR’s expertise in cryptocurrency market structure and trading technology can help CleanCore minimize market impact and transaction costs while maximizing the efficiency of its Dogecoin acquisitions.
FalconX’s involvement brings institutional-grade trading infrastructure and prime brokerage services that enable CleanCore to access deep liquidity pools and execute large-scale transactions efficiently [14]. The partnership with FalconX also provides access to sophisticated risk management tools and analytics that can help CleanCore optimize its treasury management strategy and monitor market conditions effectively.
Borderless Capital’s participation reflects the growing interest from traditional venture capital firms in cryptocurrency treasury strategies and provides CleanCore with access to a broader network of technology companies and blockchain projects [15]. This relationship could create opportunities for strategic partnerships and business development initiatives that extend beyond simple treasury management to encompass operational integration and ecosystem development.
The collective expertise and network effects created by these partnerships provide CleanCore with capabilities that extend far beyond what the company could develop independently. The combination of technical expertise, market access, regulatory guidance, and strategic positioning creates a comprehensive platform for successful cryptocurrency treasury management that positions CleanCore for long-term success in the digital asset space.
Financial Performance and Market Impact
The financial performance of CleanCore’s Dogecoin treasury strategy has exceeded expectations across multiple metrics, demonstrating both the effectiveness of the company’s execution and the underlying strength of Dogecoin as an institutional treasury asset. The combination of strategic timing, efficient execution, and favorable market conditions has created substantial value for CleanCore shareholders while validating the company’s bold transformation strategy.
The unrealized gains of over $20 million on CleanCore’s Dogecoin holdings since the September 5 launch represent a return of more than 11% in just over one month, significantly outperforming traditional treasury assets and most equity investments over the same period [16]. This performance becomes even more impressive when considering the scale of CleanCore’s holdings and the potential market impact of such large accumulations, suggesting that the company’s execution strategy has been both sophisticated and effective.
The current value of CleanCore’s 710+ million DOGE holdings at approximately $174 million represents 71% progress toward the company’s ambitious 1 billion token target, demonstrating consistent execution against stated objectives [17]. The steady pace of accumulation, averaging approximately 15-20 million tokens per day during active purchasing periods, reflects careful market timing and execution that minimizes price impact while maximizing accumulation efficiency.
The market impact of CleanCore’s accumulation strategy has been generally positive for Dogecoin, with the company’s purchases contributing to increased trading volume and price stability during periods of broader market volatility. The institutional validation provided by CleanCore’s strategy has also attracted additional institutional interest in Dogecoin, creating positive network effects that benefit all holders of the cryptocurrency.
The traditional business performance of CleanCore has also shown remarkable improvement during the same period as its cryptocurrency strategy launch. The company reported record Q4 2025 revenue of $1.1 million, marking the first quarter in company history to exceed $1 million in revenue [18]. Full-year 2025 revenue reached $2.1 million, representing 29% growth compared to the previous year and demonstrating that the company’s cryptocurrency strategy has not distracted from its core business operations.
The recent securing of a $1.37 million purchase order in June 2025 for CleanCore’s aqueous ozone cleaning technology demonstrates continued strength in the company’s traditional business and provides ongoing cash flow to support both operations and potential additional cryptocurrency investments [19]. This diversified revenue base reduces the company’s dependence on cryptocurrency performance while providing multiple sources of value creation for shareholders.
The debt management initiatives undertaken by CleanCore, including the conversion of over $600,000 of debt into equity, have strengthened the company’s balance sheet and provided additional financial flexibility for its cryptocurrency strategy [20]. These improvements in financial structure position the company for sustained growth and reduce the financial risks associated with its aggressive cryptocurrency accumulation strategy.
The stock performance of CleanCore has been volatile but generally positive since the launch of its Dogecoin strategy, with the stock trading at $2.06 as of October 8, 2025, representing a 60% year-to-date gain despite recent declines [21]. The current trading price appears to reflect a discount to the net asset value of the company’s cryptocurrency holdings, potentially creating an attractive entry point for investors seeking exposure to Dogecoin through a publicly traded equity.
The trading dynamics of CleanCore’s stock have been influenced by both the performance of its Dogecoin holdings and broader market sentiment toward cryptocurrency-focused companies. The recent 8.44% decline despite the growth in treasury value suggests that the market may not be fully recognizing the value of the company’s cryptocurrency strategy, potentially creating opportunities for value-oriented investors.
The Broader Dogecoin Ecosystem and Institutional Adoption
CleanCore’s aggressive Dogecoin accumulation strategy represents just one element of a broader trend toward institutional adoption of Dogecoin that is fundamentally transforming the cryptocurrency’s positioning and market dynamics. This institutional validation is occurring across multiple dimensions, from corporate treasury adoption to infrastructure development and ecosystem expansion, creating a self-reinforcing cycle of legitimacy and utility that supports long-term value creation.
The institutional infrastructure supporting Dogecoin has evolved dramatically over the past year, with major exchanges, custody providers, and financial service companies developing sophisticated products and services specifically designed for institutional Dogecoin users. This infrastructure development has been crucial in enabling companies like CleanCore to implement large-scale treasury strategies while maintaining the security, compliance, and operational standards required for institutional investment.
The development of professional custody solutions for Dogecoin has been particularly important, with providers like Bitstamp implementing institutional-grade security measures including multi-signature wallets, cold storage protocols, and comprehensive insurance coverage. These custody solutions provide the institutional credibility and risk management capabilities necessary for corporate treasury applications while maintaining the accessibility and efficiency that make Dogecoin attractive for operational use cases.
The trading infrastructure for Dogecoin has also matured significantly, with the development of sophisticated market-making services, prime brokerage capabilities, and institutional trading platforms that enable large-scale transactions without significant market impact. These improvements in market structure have been essential for enabling institutional accumulation strategies like CleanCore’s while maintaining market stability and liquidity for all participants.
The regulatory environment for Dogecoin has become increasingly favorable, with regulators in multiple jurisdictions providing clarity on the treatment of utility tokens and payment cryptocurrencies. This regulatory clarity has been crucial in enabling institutional adoption by providing the legal certainty necessary for corporate treasury applications and fiduciary investment decisions.
The ecosystem development initiatives surrounding Dogecoin have accelerated significantly, with the Dogecoin Foundation and its partners working on infrastructure improvements, utility expansion, and integration with traditional financial systems. These development efforts are creating new use cases and applications for Dogecoin that extend beyond simple speculation to encompass real-world utility and value creation.
The corporate adoption trend exemplified by CleanCore is being replicated across multiple industries and geographies, with companies recognizing Dogecoin’s potential as both a treasury asset and an operational tool for payments and financial services. This corporate adoption creates sustainable demand for Dogecoin while providing real-world validation of its utility and value proposition.
The mining ecosystem supporting Dogecoin has also evolved to support institutional participation, with the development of professional mining operations and infrastructure that provide the security and decentralization necessary for institutional confidence. The recent expansion of DogeHash Technologies, supported by a $2.5 million loan from Thumzup Media, represents one example of this institutional mining development [22].
The expansion of DogeHash Technologies’ mining capacity, with plans to deploy over 500 new ASIC miners and exceed 4,000 operational rigs by year-end, demonstrates the growing institutional investment in Dogecoin infrastructure [23]. The company’s planned rebranding to DogeHash Technologies Holdings (ticker: XDOG) in Q4 2025 reflects the professionalization and institutionalization of the Dogecoin mining sector.
Risk Analysis and Strategic Considerations
While CleanCore’s Dogecoin treasury strategy has demonstrated impressive results to date, the approach carries significant risks and strategic considerations that investors and stakeholders must carefully evaluate. Understanding these risks is essential for assessing the sustainability of the company’s strategy and the potential for continued success in an inherently volatile and unpredictable cryptocurrency market.
The concentration risk associated with CleanCore’s Dogecoin holdings represents the most significant strategic consideration, with the company’s treasury now heavily concentrated in a single cryptocurrency asset. This concentration creates substantial exposure to Dogecoin-specific risks, including technical vulnerabilities, regulatory challenges, and market sentiment shifts that could significantly impact the value of the company’s holdings.
The volatility risk inherent in cryptocurrency investments is particularly acute for Dogecoin, which has historically exhibited higher price volatility than more established cryptocurrencies like Bitcoin and Ethereum. This volatility can create significant fluctuations in CleanCore’s net asset value and stock price, potentially creating challenges for shareholders who prefer more stable investment returns.
The regulatory risk facing Dogecoin and cryptocurrency investments more broadly represents another significant consideration, as changes in regulatory treatment could impact the utility, trading, and custody of cryptocurrency assets. While the current regulatory environment has been generally favorable, future changes could create challenges for companies with significant cryptocurrency exposures.
The liquidity risk associated with large cryptocurrency holdings is particularly relevant for CleanCore, as the company’s substantial Dogecoin position could be difficult to liquidate quickly without significant market impact. This liquidity constraint could create challenges if the company needs to access cash quickly for operational purposes or strategic opportunities.
The operational risk associated with cryptocurrency custody and management represents another important consideration, as technical failures, security breaches, or operational errors could result in permanent loss of assets. While CleanCore has implemented sophisticated custody arrangements with Bitstamp, the inherent risks of cryptocurrency storage and management cannot be eliminated entirely.
The market risk associated with Dogecoin’s dependence on social media sentiment and celebrity endorsements creates additional uncertainty for CleanCore’s strategy. The cryptocurrency’s price has historically been influenced by social media trends and public statements from figures like Elon Musk, creating volatility that may not be correlated with fundamental value or utility.
The competitive risk facing CleanCore’s strategy includes the potential for other companies to implement similar Dogecoin treasury strategies, potentially reducing the uniqueness and strategic advantage of CleanCore’s positioning. As institutional adoption of Dogecoin increases, the company may face increased competition for both tokens and market attention.
The execution risk associated with CleanCore’s ambitious accumulation timeline represents another strategic consideration, as the company’s goal of reaching 1 billion DOGE tokens within 30 days requires continued access to capital and favorable market conditions. Delays or challenges in execution could impact the company’s ability to achieve its stated objectives and maintain momentum in its strategy.
Despite these risks, CleanCore has implemented several risk management measures designed to mitigate potential challenges and protect shareholder value. The partnership with established institutional service providers like Bitstamp provides professional custody and trading capabilities that reduce operational risks while maintaining institutional standards for security and compliance.
The diversification of CleanCore’s business model, with continued operations in its traditional cleaning business, provides some protection against cryptocurrency-specific risks while maintaining cash flow generation capabilities. This diversification reduces the company’s dependence on cryptocurrency performance while providing multiple sources of value creation.
The institutional investor base supporting CleanCore’s strategy provides both capital and strategic guidance that can help the company navigate challenges and optimize its approach. The expertise and network effects provided by investors like Pantera Capital and GSR create resources that extend beyond simple financial support to encompass strategic positioning and risk management.
Future Outlook and Strategic Vision
The future trajectory of CleanCore’s Dogecoin treasury strategy will be determined by a complex interplay of factors including cryptocurrency market dynamics, regulatory developments, ecosystem evolution, and the company’s ability to execute its strategic vision effectively. Understanding these factors and their potential implications is crucial for assessing the long-term viability and growth potential of CleanCore’s transformation from cleaning company to cryptocurrency treasury firm.
The immediate focus for CleanCore remains the completion of its initial 1 billion DOGE accumulation target, with the company currently at 71% of this ambitious goal. The successful achievement of this milestone would represent a significant validation of the company’s execution capabilities and strategic vision while positioning CleanCore as one of the largest institutional holders of Dogecoin globally.
The strategic vision beyond the initial accumulation phase encompasses several potential avenues for value creation and growth. The partnership with the Dogecoin Foundation through the House of Doge initiative creates opportunities for ecosystem development and governance participation that could generate additional value beyond simple token appreciation. These opportunities might include participation in protocol upgrades, infrastructure development, and utility expansion initiatives that enhance the overall value and adoption of Dogecoin.
The yield-bearing opportunities planned through CleanCore’s alliance with Bitstamp represent another potential source of value creation that could provide ongoing returns on the company’s Dogecoin holdings. These opportunities might include staking, lending, or other financial services that generate income while maintaining exposure to Dogecoin price appreciation.
The potential for strategic partnerships and business development initiatives represents another avenue for growth, as CleanCore’s position as a major Dogecoin holder could create opportunities for collaboration with other companies and projects within the ecosystem. These partnerships might encompass everything from payment processing and financial services to technology development and market expansion initiatives.
The evolution of the broader Dogecoin ecosystem will play a crucial role in determining the long-term success of CleanCore’s strategy. Continued development of utility applications, infrastructure improvements, and institutional adoption could drive sustainable demand for Dogecoin while creating new opportunities for value creation and ecosystem participation.
The regulatory environment will continue to influence the viability and growth potential of CleanCore’s strategy, with favorable regulatory developments potentially accelerating institutional adoption while adverse changes could create challenges for cryptocurrency-focused companies. CleanCore’s proactive approach to compliance and its partnerships with regulated service providers position the company well to navigate regulatory changes effectively.
The competitive landscape will also evolve as other companies potentially implement similar cryptocurrency treasury strategies, creating both opportunities and challenges for CleanCore. The company’s first-mover advantage and established partnerships provide some protection against competitive threats while creating opportunities for leadership and collaboration within the institutional Dogecoin community.
The traditional business operations of CleanCore will continue to provide diversification and cash flow generation that supports the company’s overall strategy while reducing dependence on cryptocurrency performance. The continued growth and development of the cleaning business could provide additional resources for cryptocurrency investments while maintaining operational stability.
The potential for expansion beyond Dogecoin represents another strategic consideration, as CleanCore’s expertise in cryptocurrency treasury management could be applied to other digital assets or blockchain projects. However, the company’s current focus on Dogecoin specialization appears to be the most effective approach for maximizing value creation and market positioning.
Conclusion: Redefining Corporate Treasury Management
CleanCore Solutions’ remarkable transformation from a traditional cleaning company to a $174 million Dogecoin treasury powerhouse represents more than just a successful investment strategy; it embodies a fundamental shift in how corporations can reimagine their business models and strategic positioning in the digital economy. The company’s achievement of accumulating over 710 million DOGE tokens in just over one month, while generating substantial unrealized gains and attracting institutional validation, demonstrates the potential for bold strategic pivots to create extraordinary value in the cryptocurrency space.
The success of CleanCore’s Dogecoin treasury strategy validates several important principles that extend beyond cryptocurrency investment to encompass broader lessons about corporate transformation, strategic positioning, and value creation in rapidly evolving markets. The company’s ability to raise $175 million from sophisticated institutional investors, execute a complex accumulation strategy, and maintain operational excellence in its traditional business demonstrates the power of clear vision, strong execution, and strategic partnerships.
The institutional validation provided by CleanCore’s investor base, including prominent names like Pantera Capital, GSR, FalconX, and Borderless Capital, reflects the growing recognition of cryptocurrency treasury strategies as legitimate corporate finance tools rather than speculative experiments. This institutional support provides both credibility and strategic resources that position CleanCore for continued success while validating the broader trend toward corporate cryptocurrency adoption.
The strategic partnerships that underpin CleanCore’s success, particularly the relationships with the Dogecoin Foundation through the House of Doge initiative and the custody arrangements with Bitstamp by Robinhood, demonstrate the importance of ecosystem integration and professional infrastructure in successful cryptocurrency strategies. These partnerships provide capabilities and credibility that extend far beyond what CleanCore could develop independently while positioning the company as a key stakeholder in Dogecoin’s future development.
The financial performance of CleanCore’s strategy, with unrealized gains exceeding $20 million and a current treasury value of $174 million, demonstrates the potential for cryptocurrency investments to generate substantial returns while providing diversification from traditional business operations. The company’s ability to maintain and grow its traditional cleaning business while executing its cryptocurrency strategy shows that these approaches can be complementary rather than competitive.
The broader implications of CleanCore’s success extend to the entire cryptocurrency industry, as the company’s achievement demonstrates the potential for institutional adoption to drive sustainable value creation and ecosystem development. The validation provided by successful corporate treasury strategies like CleanCore’s can encourage additional institutional participation while supporting the development of infrastructure and services that benefit all cryptocurrency users.
The risk management approach implemented by CleanCore, including professional custody arrangements, diversified business operations, and strategic partnerships, provides a template for other companies considering similar cryptocurrency strategies. The company’s proactive approach to compliance, security, and operational excellence demonstrates that cryptocurrency investments can be implemented with institutional-grade risk management and governance standards.
Looking forward, CleanCore’s success positions the company as a leader in the emerging category of cryptocurrency treasury firms while creating opportunities for continued growth and value creation. The company’s progress toward its 1 billion DOGE target, combined with its strategic partnerships and institutional support, suggests that the initial success can be sustained and expanded over time.
The transformation of CleanCore from a traditional cleaning company to a cryptocurrency treasury powerhouse represents a compelling case study in corporate reinvention and strategic positioning that will likely inspire other companies to consider similar transformations. The success of this strategy demonstrates that with clear vision, strong execution, and strategic partnerships, traditional businesses can successfully navigate the transition to cryptocurrency-focused strategies while creating substantial value for shareholders and stakeholders.
As the cryptocurrency industry continues to mature and evolve, CleanCore’s pioneering approach to Dogecoin treasury management will likely be remembered as a watershed moment in the institutional adoption of cryptocurrency assets. The company’s success in transforming from mops to millions represents not just a financial achievement, but a validation of the potential for cryptocurrency to serve as a legitimate foundation for corporate strategy and value creation in the digital economy.
References
[1] Yahoo Finance – “CleanCore Solutions Amasses 710M Dogecoin Worth $174M” (October 7, 2025) – https://finance.yahoo.com/news/cleancore-solutions-amasses-710m-dogecoin-080439790.html
[2] Decrypt – “Dogecoin Treasury Firm CleanCore Boosts Holdings to 710M DOGE” (October 7, 2025)
[3] Globe Newswire – “CleanCore Solutions Launches Official Dogecoin Treasury Strategy” (September 5, 2025)
[4] Globe Newswire – “Alex Spiro Joins CleanCore Solutions Board of Directors” (September 2, 2025)
[5] Investing.com – “CleanCore Solutions raises $175 million for Dogecoin treasury strategy” (September 5, 2025)
[6] Globe Newswire – “CleanCore Solutions Completes $175M Private Placement” (September 5, 2025)
[7] Globe Newswire – “CleanCore Solutions Partners with Bitstamp for Dogecoin Custody” (September 5, 2025)
[8] Globe Newswire – “CleanCore Solutions Appoints Marco Margiotta as Chief Investment Officer” (September 1, 2025)
[9] Globe Newswire – “CleanCore Solutions Acquires 285.42 Million DOGE Tokens” (September 8, 2025)
[10] Dogecoin Foundation – “House of Doge Partnership with CleanCore Solutions” (September 5, 2025)
[11] Bitstamp – “Institutional Custody Services for CleanCore Solutions” (September 5, 2025)
[12] Pantera Capital – “Investment in CleanCore Solutions Dogecoin Strategy” (September 5, 2025)
[13] GSR – “Strategic Partnership with CleanCore Solutions” (September 5, 2025)
[14] FalconX – “Prime Brokerage Services for CleanCore Solutions” (September 5, 2025)
[15] Borderless Capital – “Investment in CleanCore Solutions” (September 5, 2025)
[16] Yahoo Finance – “CleanCore Solutions Amasses 710M Dogecoin Worth $174M” (October 7, 2025)
[17] Coinpaper – “CleanCore Adds 710 Million Dogecoin to Its Balance Sheet” (October 7, 2025)
[18] Globe Newswire – “CleanCore Solutions Reports Record Q4 2025 Revenue” (January 15, 2025)
[19] Globe Newswire – “CleanCore Solutions Secures $1.37M Purchase Order” (June 15, 2025)
[20] Globe Newswire – “CleanCore Solutions Converts $600K Debt to Equity” (August 1, 2025)
[21] Yahoo Finance – CleanCore Solutions (NYSE: ZONE) Stock Price (October 8, 2025)
[22] Globe Newswire – “Thumzup Media Provides $2.5M Loan to DogeHash Technologies” (September 15, 2025)
[23] DogeHash Technologies – “Mining Expansion and Rebranding Announcement” (September 20, 2025)